The latest cyber threat, nicknamed WannaCry, is a big deal and has had global consequences. Here’s what you need to know about it and how Upward Technology can help you steer the ship in terms of disaster mitigation…
By Systems Tech, Paul Schopfer

If you are reading this, you are likely aware that one of the worst cyber attacks ever to hit the Information Technology industry is in progress as of the date of this blog. The current global incident involves a newer kind of attack, with a twist: not only does it encrypt files on a Windows computer and hold data ransom, it also uses a recently discovered vulnerability in the most widely used operating systems in today’s business world to replicate and infect other systems over the network – meaning any network connected, unpatched Windows machine is at risk of infection. This is a big deal.
While the impact is yet to be fully realized, among the tens of thousands of verified infected systems are several large healthcare systems. First, the good news: private patient data is not likely to be lost, as it is not normally stored on Windows PC’s but on database servers running other operating systems which are backed up in most cases – ready to be restored to a time before an infection took place. The impact is mainly to daily operations, such as scheduling and electronic record keeping, and most hospitals have downtime procedures to see them through the outages with minimal interruption to patient care for existing patients.
The bad news? It all could have been prevented. Microsoft released updates to its Windows operating system before the attacks, and news of the vulnerability was readily available in this case. The patch to eliminate the vulnerability in affected systems was made available to every internet-connected Windows machine via Windows Update, which by default is configured to automatically download and install patches to the system.
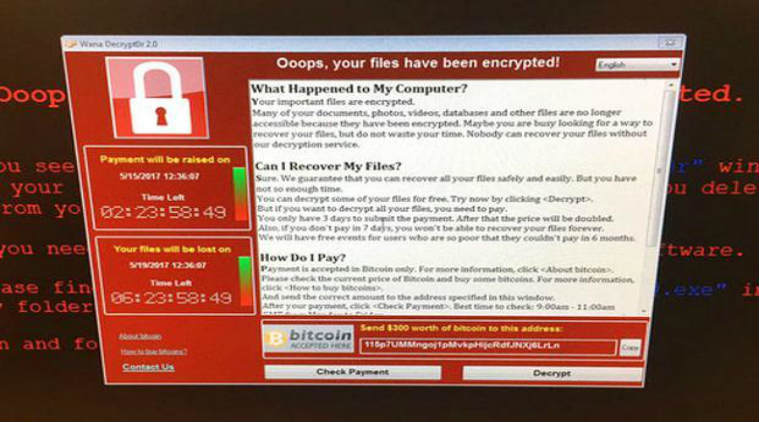
An example of what the attack looks like…
So, the obvious question here is: why did this become a global catastrophe? It happened because systems weren’t patched against the vulnerability before hackers released an exploit into the wild.
From my prior experience as a consultant implementing healthcare IT systems, I have some educated guesses why this was the case for many of the businesses which were impacted: Healthcare, in particular, is an industry that is resistant to rapid change and systems managers are understandably cautious of patches – which can introduce unknown issues into the patient care and electronic record keeping systems. Automatic updates on servers and workstations are often disabled, and patches are regularly delayed until equipment and software vendors indicate there are no issues, and then releases are tested internally before being scheduled for roll out. This vetting process can take months, or even years in some cases, due to the need to ensure continuity of business as well as train users and in some cases to maintain certification for equipment and workflows critical to patient care.
It is critical to validate patches before rolling them out to systems to prevent loss of productivity and revenue from downtime resulting from bad or failed patches. It is also critical to make sure people can work effectively without interruption to maximize productivity and profits.
This is often the conflict we find between productivity and safety: with vulnerabilities and new attack vectors being discovered so rapidly by both ethical and hostile programmers, it is a constant struggle to keep machines patched before they are compromised. And it is equally hard to educate users not to ignore the constant flood of update warnings for every software application they use. This is particularly true of systems which are in use around the clock: it is difficult to schedule downtime to do updates when it interferes with work in progress.
So what’s a business to do?
We at Upward Technology believe that a balanced best-practices strategy is required to successfully mitigate cyber disasters, which can come from a variety of sources ranging from power failure to hardware issues to cyber attacks. You need a solid systems solution, including physical documentation, automated patch management, antivirus, antimalware, backup and disaster recovery. Here are a few of the many things we do every day for our customers to ensure they are protected:
- Adhering to vendor “best practices” for building and securing systems, including password management as well as software configuration and updates. Subscribing to vendor-supported update services where available.
- Providing managed multi-tiered backup systems which allow for existing systems to be backed up without user intervention, and to be recovered with a minimum of downtime once a disaster has passed.
- Using automated patch management for applications and operating systems, to ensure managed servers and workstations are updated on a schedule, pushing critical updates when they are released from any software vendor used by our customers.
- Reviewing system logs for errors related to patch installations and having monitoring in place for notifications in the event systems are not being actively protected or are out of compliance with company security standards.
- Providing access to skilled and trustworthy technicians to ensure questions and issues related to security are handled correctly and efficiently as they arise.
- Proactively monitoring for emerging threats and security trends, using a variety of resources such as tech blogs and vendor bulletins and keeping an active dialog with our vendors and customers to develop and maintain the best defense strategies available.
- To decrease the stress of unexpected outages, provide alternate options to our user communities, such as access to email and the company’s VOIP system from their cell phones and cloud-based virtual desktop systems for products that can be accessed from alternate locations, when internal systems are unavailable.
The systems side of the equation is well understood if not well implemented, and the global business community spends billions of dollars toward disaster mitigation every year. The human side is sometimes neglected, and all too often do we talk to companies who rely too heavily on their systems or people alone to eliminate issues. Businesses need to focus on both components to truly survive and thrive during the inevitable loss of access that happens during downtime events resulting from any cause, security or otherwise. Training users how to avoid and recover from outages with minimal intervention by the folks managing and supporting their systems is essential to a complete disaster mitigation strategy.
Despite huge amounts of data that show we need better security, the effectiveness and impact of recent disastrous global cyber attacks show clearly that in many cases businesses lack clear understanding that an occasional major incident is often far more damaging to a company’s bottom line than are occasional proactive interruptions to patch programs and update security measures as new threats are discovered. When choosing your company’s IT support vendor, it is important to be sure they thoroughly understand your environment and have the expertise to effectively work with your business to plan and implement a best-practices disaster mitigation strategy that fits your unique culture and environment.
Want to chat more about how your business could benefit by putting some of these plans in place while also tightening up on security as a whole? Contact Upward Technology today! Thanks for reading!
Leave A Comment